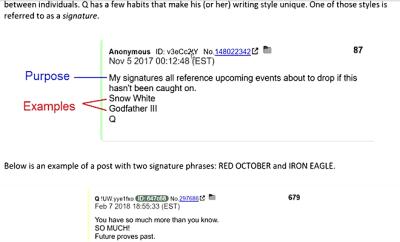
NWO
SPIES HACKED COMPUTERS W/ SECRET WARRANTS, STRETCHING U.K. LAW
by Andrew Fishman & Glenn Greenwald, The Intercept:
British spies have received government permission to intensively study software programs for ways to infiltrate and take control of computers. The GCHQ spy agency was vulnerable to legal action for the hacking efforts, known as “reverse engineering,” since such activity could have violated copyright law. But GCHQ sought and obtained a legally questionable warrant from the Foreign Secretary in an attempt to immunize itself from legal liability.
GCHQ’s reverse engineering targeted a wide range of popular software products for compromise, including online bulletin board systems, commercial encryption software and anti-virus programs. Reverse engineering “is essential in order to be able to exploit such software and prevent detection of our activities,” the electronic spy agency said in a warrant renewal application.
But GCHQ’s hacking and evasion goals appear to have led it onto dubious legal ground and, at times, into outright non-compliance with its own procedures for staying within the bounds of the law. A top-secret document states that a GCHQ team lapsed in following the agency’s authorization protocol for some continuous period of time. Meanwhile, GCHQ obtained a warrant for reverse engineering under a section of British intelligence law that does not explicitly authorize — and had apparently never been used to authorize — the sort of copyright infringement GCHQ believed was necessary to conduct such activity.
The spy agency instead relied on the Intelligence Services Commissioner to let it use a law pertaining only to property and “wireless telegraphy,” a law that had never been applied to intellectual property, according to GCHQ’s own warrant renewal application. Eric King, deputy director of U.K. surveillance watchdog Privacy International said, after being shown documents related to the warrant, “The secret reinterpretation of powers, in entirely novel ways, that have not been tested in adversarial court processes, is everything that is wrong with how GCHQ is using their legal powers.”
GCHQ may have also circumvented a restriction on using the type of warrant it obtained for domestic purposes; the agency said in one memo that it has used reverse engineering to support “police operations” and the domestic policing-focused National Technical Assistance Centre.
The agency also described efforts to cozy up to dozens of government staffers it believed could help obtain further warrants.
The agency’s slippery legal maneuvers to enable computer hacking call into question U.K. government assurances about mass surveillance. To assuage public concern over such activity, the government frequently says spies are subject to rigorous oversight, including an obligation to obtain warrants. As it turns out, such authorizations have, at times, been vague and routine, as demonstrated by top-secret memos prepared by GCHQ in connection with the reverse engineering warrant.
The controversial path GCHQ took to authorize reverse engineering also seems likely to lend momentum to an ongoing push to reform the way surveillance warrants are issued in the U.K. Earlier this month, the U.K.’s independent reviewer of terrorism legislation, David Anderson, issued areport recommending that “all warrants should be judicially authorised” and describing the current regulatory system as “undemocratic, unnecessary and — in the long run — intolerable.”
This story is based on 22 documents from NSA whistleblower Edward Snowden, linked below. None have been published before. One was briefly described in a January story in The Guardian.